Here is our Long Distance RFID Fixed Reader for Ear Tag. This fixed reader has big antenna. It reads about 35-45cm if you use FOFIA ear tags. This fixed reader can be used together with some feeding equipment , milking equipment or Weighing system.
RLF102A is a middle distance ISO11784/ISO11785 tag reader produced by Wuxi Fofia Tech. The reading distance can be more than 35cm if using Fofia`s ear tag. It supports RS232& RS485 output.
Wuxi Fofia Technology Co., Ltd is a company that provides complete solutions of livestock smart management and pet ID management. Our products can be used for all farm animals, pets, fish, Arowana and wild animals.
We`re committed to the development and promotion of animal identification products. We win customers` trust with our high-quality products,first-class service and fast delivery time. All our raw material are from qualified supply, the quality can be guaranteed.
We are specialized in production of animal ID products,animal microchips,pet microchips, ear tags, electronic ear tags and RFID reader for more than 20 years.
Fixed Reader, RFID Fixed Reader,Cow fixed Reader Wuxi FOFIA Technology Co.,Ltd. , https://www.fofiatag.com
With the development of network technology and the intensification of information construction, the security requirements for the perimeter of the market are continuously increasing, and the demand for the technology loopholes in solving the core system of the security industry is most obvious. Market demand has spawned innovative perimeter security products, and the fifth generation of pulsed electronic fence products—“T6/T8 series touch screen anti-bypass pulse electronic fence host†emerged. T6/T8 series electronic fencing host uses Smart DEC intelligent algorithm (full name "anti-potential equalization cracking technology"), adds single-line touch network alarm, anti-bypass alarm function, ending the long-standing two major technological loopholes in the electronic fence industry, and It can greatly reduce the false alarm rate by identifying the front-end touch screen signal. From the user's point of view, the fifth generation of pulsed electronic fence hosts has greatly improved the user experience. The development and application of electronic fence technology has entered the next milestone era. 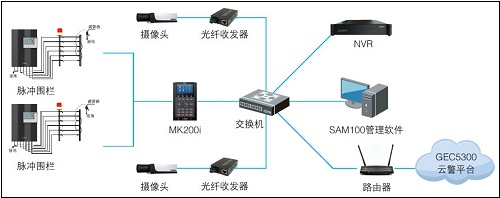
The past life of the pulsed electronic fence
The development of electronic fences can be traced back to the 1920s and 1930s. From the most primitive ranch fences to the evolution of the fifth-generation intelligent touch-net-bypass-type pulsed electronic fences, this is undoubtedly the numerous technological revolutions of the electronic fences over the past 100 years. Achievements.
The first stage: the electronic enclosure of the ranch The earliest electronic fence originated from the mobile ranch in England and England. The shepherd pulled a wire and connected it with direct current to form a simple electronic fence for the purpose of grazing so that the animals could move within a certain range. After the war, in Europe, the proportion of animal husbandry in agriculture was very high, and a large number of animal husbandry market demands promoted the development and promotion of “electronic fencesâ€. Cattle and sheep encountered the electric fence of the “electronic fence†and returned it, playing a good role as a “shepherdâ€. At the same time, they also prevented large animals or beasts running outside the circle from entering. This played a major role in the development of the animal husbandry at the time. The promotion is still playing a greater role in some countries where animal husbandry is more developed. It is tentatively considered the embryonic form of the first generation of electronic fence products.
Phase II: Alarm Electronic Fence Along with the development and deepening of the entire “electronic fence†industry, more and more product accessories and types, intelligent perimeter security alarm system with blocking and alarm functions in the middle and late 90s, began professional use. In the field of social public safety, it has the functions of open circuit, short circuit and power failure alarm, and it also upholds the safety barrier function of electronic fences. The product fully considers people's initiative and wisdom, can accurately determine the unintentional touch, intentional destruction, illegal intrusion and other conditions, is a better choice for the perimeter security project.
The third stage: intelligent electronic fence As people's requirements for product performance and function are getting higher and higher, products need to be more humane, and products with more functions begin to appear. The output pulse voltage of the second generation product is constant. When the perimeter changes, the voltage of the front end will be too high or too low with the length of the perimeter; at the same time, when the product is installed in a villa or community with a low wall False strikes to children or nearby workers occur during the day. Based on the above issues, the third-generation adjustable output voltage and products that can set high-voltage mode, safe mode switching function into the market, such as G3/T5 series pulse electronic fence host, it has open circuit, short circuit, power failure alarm function and uphold The security barrier function of the electronic fence fully takes into account human initiative and wisdom, and can accurately determine various situations such as unintentional touching, intentional destruction, and illegal intrusion. At the same time, the products at this stage also have remote control, remote operation, and other functions, providing better products for large-scale applications in villas and communities.
Phase IV: Network Electronic Fencing With the gradual deepening of the Internet of Things in the security industry, most of the perimeter alarm systems still remain on the front-end alarm and single device control management, and there is a defect that linkage cannot be performed, resulting in the security system being in “ Decentralized management. As a result, the network electronic fence came into being. Taking the G5S/G5P series pulsed electronic fence host as an example, the main node device's entire network of electronic fence hosts, intelligent control terminals and management software can be directly connected to Ethernet. Users can access the network through the network. Supervise the electronic fence and realize the functional requirements of real-time information transmission, data interaction and remote supervision. The degree of network and integration of the fourth-generation products has reached an unprecedented level of maturity, and has the characteristics of flexible solutions, simple construction, cost savings, and stable transmission.
Three-year sword's technological breakthrough
Intelligent perception of magnetic field balance waves, make up for technical loopholes Pulse electronic fence is transmitted through the host's launch port to the alloy wire on the front fence, and the receiving end receives the pulsed electrical signal, so that the electronic fence system forms a complete circuit. Once a person has invaded, resulting in a short circuit between two adjacent alloy wires or someone deliberately destroying the front-end fence alloy wire (open circuit), the pulse electronic fence host will promptly send an alarm and send it to the control center through the communication line.
In the current booming industry of pulsed electronic fencing, there are two fatal technical drawbacks that have plagued industry practitioners for many years: single-wire touch network does not alarm and bypass bypass does not alarm, which brings users a great security risk.
Although current single-wire touch screens of pulsed electronic fence products on the market can produce electric shocks to intruders, some products also generate alarms when the resistance is small, but they do not alarm when the resistance is high. This means that when an intruder wears sneakers or a plastic glove to climb the fence in a single line, the electronic fence on the market will not generate an alarm, and the insulant's insulation material can also prevent him from suffering an alarm. The electric shock on the front fence had caused it to successfully climb over the wall and there were serious loopholes in the prevention. 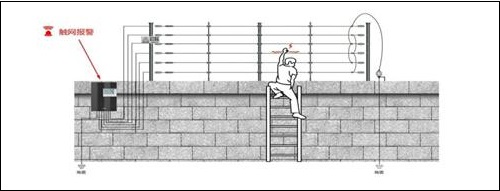
Bypassing the bypass without warning is another technical drawback of the existing electronic fence. The bypass bridges are divided into single-line bypass bridges (Figure 1) and loop bypass bridges (Figure 2). When intruders use short-circuit lines to connect the two ends of the metal fence at the front end of the electronic fence respectively (single-line bypass bridges ), or use two (four) short-circuit wires to connect the spaced metal wires (circuit bypass bypass) at the jumper connection of the fence network, and the failure area is generated at the front end of the electronic fence, and when the metal wire in the failure area is cut off If the host does not call the police, the intruder can use this "loophole" to climb over the fence and cause property damage. 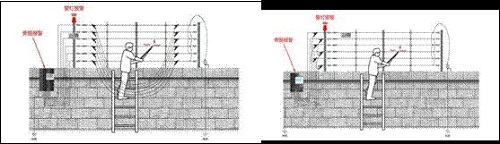
In order to make up for the defects of electronic fences and increase customer safety, Shanghai Guang Tuo successfully developed a new T6/T8 series of touch-net anti-bypass pulsed electronic fences that took 3 years to complete, using the SmartDEC intelligent algorithm (full name, "anti-potential cracking" The technology ") can realize the four alarm modes of single-wire touch alarm, anti-bypass alarm, short-circuit alarm and open circuit alarm by identifying the front-end touch net situation, which truly solves the long-standing technical loophole and improves the electronic fence. safety.
Full analysis of computing identify intrusions signal, the maximum reduction of false positives <br> <br> host on the principle of electronic fence is not allowed to have false negatives, how to reduce false positives on the basis of false negatives is not present the electronic fence technical problem to be solved . Today, reducing false positives is generally focused on the improvement of hardware, that is, the improvement of sensors and key components on the front end. The sensor is responsible for analyzing the collected signals. The more accurate the sensor analysis, the better it can exclude all kinds of false-positive signals.
From the general trend, pulsed electronic fences are constantly moving toward digital technology and become a mainstream trend. Compared with previous generations of pulsed electronic fences in hardware, the digital technology is now more and more focused on software, that is, some possible false positives, false negatives, such as small animals, wind, rain, snow and other interference Signals are modeled by software and various false alarm signals are identified by software algorithms. This reduces the chance of false alarms. In this regard, the T6/T8 series pulsed electronic fence hosts use the SmartDEC intelligent algorithm to sense the change of the magnetic field on the metal wire of the electronic fence and through a series of precise calculations to accurately determine the front-end fence's contact net situation and completely innovate the electronics. Fence alarm technology. When the front end fence is touched, the SmartDEC intelligent algorithm installed in the host computer can determine whether the human body or the small animal touches by calculating the variation of the electromagnetic field on the fence metal wire, and send an alarm signal to the control center for the human intrusion behavior. Greatly reduce the false positive rate of electronic fence products. At the same time, when the intruder uses a short-circuit method to connect the front end fence, the electromagnetic field balance on the fence wire will be destroyed. The SmartDEC intelligent algorithm accurately detects the intruder's bypass bridging behavior (including Single-wire bypass bridge and loop-bypass bridge), and immediately send alarm information to the control center, providing excellent time advantage for security personnel to handle the alarm.
Industry trends
The market revolution caused by the application of network and data
Based on the infiltration of the Internet of Things, the development trend of security in the future perimeter will inevitably be based on the user as the core design of networked, data and other features of the integrated information operating system. As the first barrier of the security system, the electronic fence needs a data system operation to judge the stability and security of the system more effectively. Industry experts generally believe that the T6/T8 series of touch screen anti-bypass pulse electronic fence host using original SmartDEC technology, intelligent identification of intruders touch the electronic fence front of a variety of alarm types, its technical design concept in front of the front perimeter intrusion The detection field has significant innovation and advanced nature.
However, the technological innovations of sensing and triggering sensing modes for intrusion detection of electronic fence hosts still cannot fully meet the growing needs of users. Perimeter security solutions also require a powerful network system integration platform, which makes the design of electronic fence hosts a consideration. Multiple communication methods. Taking the T6/T8 series host as an example, the product has built-in Ethernet, RS485 rich interface, to maximize the product communication connectivity and stability, to meet the needs of users and video surveillance systems, voice intercom systems, lighting control systems, effective integration requirements. Conveniently control the structure of the user server through intelligent keyboards or control software, such as remote zone deployment, mode switching, output voltage adjustment, sensitivity adjustment, alarm response time adjustment, etc., to smoothly achieve remote mobile security warning and management across regions.
When someone illegally climbs over the wall or destroys the fence, the pulsed electronic fence has a blocking effect. The linked video surveillance system pops up the alarm point video screen and performs video review. The mobile cloud alarm APP provided by the intelligent control terminal manages the front-end electronic fence zone information at a glance. The push mechanism ensures that the alarm information is immediately delivered, and the alarm information list makes it easy to view the alarm details and handle the alarm anytime and anywhere.
Finally, the networked architecture adopted by the electronic fencing system and the MK intelligent control terminal and the SMC3000 management platform constitute a three-tier network structure. Simply insert the network cable into the host and the fiber transceiver, and the construction cost will be reduced by at least 30%. The complexity and cost of construction.
The above is the technological innovation brought about by the networking and dataization of pulsed electronic fences. This change truly differentiates the differences in product technology and design concepts among domestic manufacturers. The technical differences in products can catch up in a relatively short period of time. The difference in design philosophy often stems from the genes that come from the manufacturers themselves. It is not simple to make up for and break through. In the era of dramatic changes in the global security market, it also validated the innovative value of the electronic fence leader's innovation and ingenuity strategy to create new value for users. 
Pulse electronic fence is a new type of high-tech intelligent perimeter alarm product that implements public safety as the most mainstream application. Compared with traditional perimeter security systems such as infrared, microwave, and electrostatic induction, pulsed electronic fences have low false alarm rates and are free of terrain and The significant advantages of environmental restrictions, safety, etc., have been widely used in the Expo, Olympic Games, substations, factories, communities, schools, villas, warehouses, airports, military bases, detention centers, prisons and other industries.
April 13, 2023